This Idiom demonstrates how to capture basic information about a single malware instance with the MAEC Package, through the use of its Malware Subject entity. While we’ll describe the basic process of creating a Package and Malware Subject here, this process is also applicable to the creation of more detailed content, such as for the capture of static or dynamic analysis results.
In this scenario, we’re characterizing a malware instance file with a name of badware.exe, size of 1024 bytes, and MD5 hash of B6C39FF68346DCC8B67AA060DEFE40C2.
The following are the important MAEC data model constructs used in this idiom:
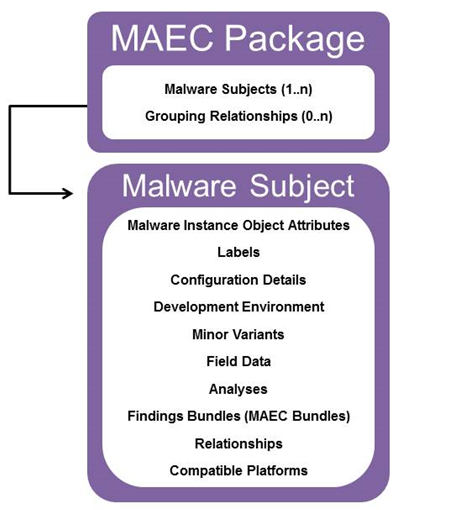
The relationship between these entities and some of their properties are highlighted in the diagram on the right. Accordingly, it would be useful to discuss each in more detail. Accordingly, let’s examine each in more detail; to start with, a MAEC Package has two required field:
id. The id field captures a globally unique identifier for the Package. The recommended form for MAEC identifier attributes is “maec-namespace-package-unique_identifier” where the namespace is optional and specified by the producer. It is recommended that the namespace be meaningful and that the identifier be a globally unique ID (GUID). For example, the identifier “maec-anubis_to_maec-act-49fd2bca-7631-4619-ba9f-2ab32b819122” uses the namespace “anubis_to_maec” to specify that the Anubis to MAEC translator tool was used to create the MAEC output. It is also recommended that the same namespace be used throughout a Package, although this is not required.
schema_version. The schema_version field specifies the version of the schema used to create the Package.
Similarly, a Malware Subject has two required fields:
id. As with the Package, the id field is required and should follow the form “maec-namespace-malware_subject-unique_identifier”.
Malware_Instance_Object_Attributes. The Malware_Instance_Object_Attributes field captures the identity of the malware instance that the Malware Subject characterizes. Its base type is the CybOX ObjectType, and therefore it has an extension point via its Properties field where the properties of one of the CybOX defined objects may be used.
Now that we’ve defined the basic properties and usage of the MAEC Package and Malware Subject, let’s build an example instance based on our scenario.
MD5 from the default CybOX vocabulary that we’ll use here, the HashNameVocab-1.0. Accordingly, Simple_Hash_Value is exactly as it sounds, and will be used to capture the MD5 hash value.This is but a small portion of what a MAEC Package and Malware Subject are able to capture. Please refer to the other Idioms for other, more detailed scenarios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<maecPackage:Malware_Subject id="example:malware_subject-36103092-46c5-4614-8096-142eebccc25b">
<maecPackage:Malware_Instance_Object_Attributes id="example:object-034e3508-0b44-4614-9e70-ffc6c5c25ac1">
<cybox:Properties xsi:type="FileObj:FileObjectType">
<FileObj:File_Name>badware.exe</FileObj:File_Name>
<FileObj:Size_In_Bytes>1024</FileObj:Size_In_Bytes>
<FileObj:Hashes>
<cyboxCommon:Hash>
<cyboxCommon:Type xsi:type="cyboxVocabs:HashNameVocab-1.0">MD5</cyboxCommon:Type>
<cyboxCommon:Simple_Hash_Value>B6C39FF68346DCC8B67AA060DEFE40C2</cyboxCommon:Simple_Hash_Value>
</cyboxCommon:Hash>
</FileObj:Hashes>
</cybox:Properties>
</maecPackage:Malware_Instance_Object_Attributes>
</maecPackage:Malware_Subject>
1
2
3
4
5
6
7
8
9
10
11
12
13
# Set up the necessary Package and Malware Subject, Analysis Bundle Instances
p = Package()
ms = MalwareSubject()
# Set the Malware_Instance_Object_Attributes on the Malware Subject
ms.malware_instance_object_attributes = Object()
ms.malware_instance_object_attributes.properties = File()
ms.malware_instance_object_attributes.properties.file_name = "badware.exe"
ms.malware_instance_object_attributes.properties.size_in_bytes = "1024"
ms.malware_instance_object_attributes.properties.add_hash("B6C39FF68346DCC8B67AA060DEFE40C2")
# Build up the full Package/Malware Subject hierarchy
p.add_malware_subject(ms)